Stanford Network Registration Tool
On this page:
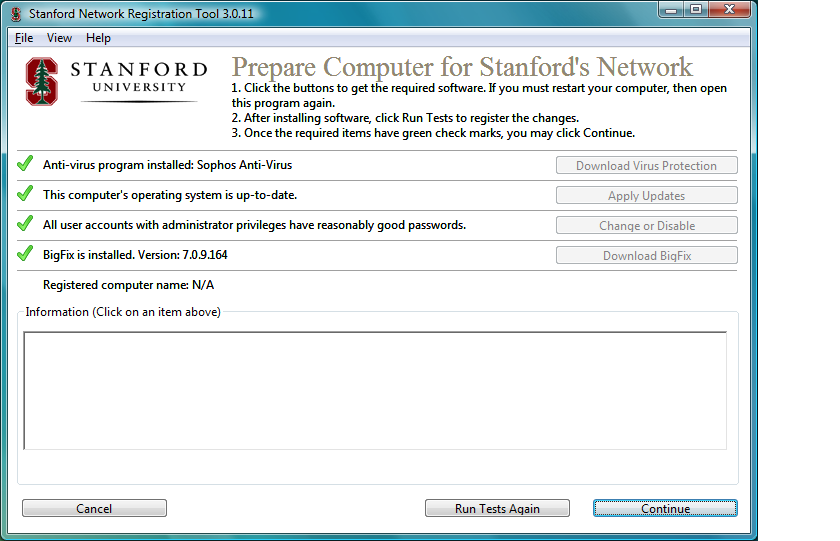
System Requirements
- Windows 2000 Service Pack 3 and above, including Windows 7, both 32- and 64-bit platforms
- Mac OS X 10.4 and above, including 10.6 (the tool might run on older versions of Mac OS X)
- Only Windows XP and above, and Mac OS X 10.4 and above, are tested and formally supported
Program Execution
- PC: If the computer is running Windows 2000 Service pack 2 or below display an error message and quit.
- Confirm that the user who is logged in has administrator rights.
- On Mac OS X and Vista the installer will prompt for administrator credentials.
- If the user does not have administrator rights display an error message and quit.
- Log all program activity to the activity log file
- Windows XP: “C:\Program Files\Common Files\Stanford\SNSR\snrt_activity_log.txt"
- Windows Vista: “C:\ProgramData\Stanford\SNSR\snrt_activity_log.txt"
- Mac OS X: “/Library/Logs/Stanford/SNSR/snrt_activity.log"
- Get all of the physical network interface hardware addresses and tag them as "wired" or "wireless."
- Download the latest configuration file from the SNSR server.
- Contact the SNSR server to get the subnet and organizational template options:
- The final completion URL (optional)
- Is BigFix required?
- Is antivirus software required?
- PC: Download the latest Microsoft Malicious Software Removal Tool.
- Skip if the most recent MSRT has already been run
- See if it is safe to check for weak administrator passwords.
Disable password strength-checking if:
- an account lockout threshold has been assigned
- an alternative authentication method (e.g., biometric) is in use
- Mac: FileVault is enabled
- Get the local computer name.
- Get the user's SUnetID (if they are authenticated to the Stanford MIT Kerberos realm).
- Get the user's login name.
- Get the operating system version.
- Get the computer Make, Model and Type.
- Get the name and version of the user's virus protection program (if a recognized
program is installed).
- PC: Information is obtained from the Windows Security Center if possible
- Mac: Only Stanford's site-licensed Sophos AV software is detected
- See if the user is missing any important patches.
- PC: critical patches as defined by Windows Update
- Mac: “recommended” Mac OS X and security updates as defined by Software Update
- Exclude any patches specified in patch_exclusions.txt on the SNSR server
- If it is safe to do so, get the names and passwords of all administrator
accounts that have been assigned weak passwords.
- If weak passwords are found, display them to the user (but do not log them), and require that they be changed
- See if BigFix has been installed.
- PC: Set the DHCP Broadcast Flag to false in discover packets on Vista.
- Estimate actual network throughput
.
- For slow links, warn users if OS patching is likely to take more than 15 minutes.
- PC: Run the Microsoft Malicious Software Removal Tool in quiet mode
- If a worm or virus was found and removed, log the fact
- Alter the UI to reflect the status of:
- virus protection
- OS security patches
- administrator passwords
- BigFix
- Display the computer's newly assigned DNS host name.
Command Button Actions
Virus Protection Download Button
Open the default browser and navigate to the appropriate web page for AV downloads. The URL is read from the configuration file.
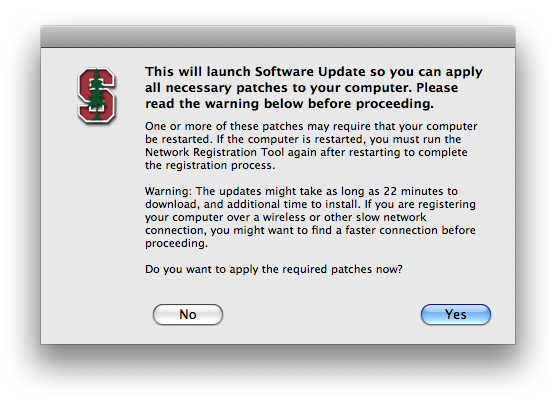
Software Update Button
PC: Patching is performed automatically using the Windows Update service.
Mac: Launch the “Software Update” application.
Warn if patch download and installation will likely take more than 15 minutes:
Change Passwords Button
Load a window that will allow the user to change weak passwords:

Download BigFix Button
Open the default browser and navigate to the appropriate web page. The URL is read from the configuration file.
Cancel Button
Ask the user if they really want to exit because the computer will not be registered if they do. If they confirm that they really want to exit, then end the program.
Run Tests Again
If the user is required to patch the computer before registering, this button will appear. If a reboot is not required, they can click on “Run Tests Again” to check for compliance. If all required patches are found, they will be able to continue with registration.
Continue Button
PC: Make the registry changes necessary to security-harden the computer
PC and Mac: Build an HTTP GET URL containing the computer MAC addresses ("MAC") appropriately tagged as "wired" and "wireless," OS version ("OS"), IP Addresses ("IP"), Make of the computer ("MAKE"), Model of the computer ("MODEL"), and Computer Type ("TYPE"), and send it to the server.
Menu Commands
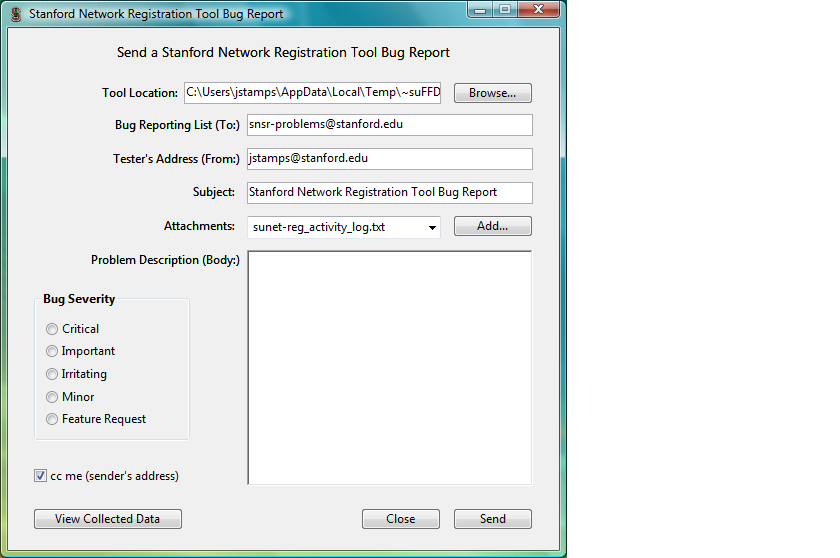
Help Menu "Send Bug Report...":
Weak Password List
The following words among others will be used when attempting to guess the administrator account passwords. All words will be attempted using lowercase (e.g., “my password”), uppercase (e.g., “MY PASSWORD”), and mixed case (e.g., “My Password"). In addition to this short list, a longer list of more than 1000 passwords will be used when possible.
- “”
- “guest”
- “password”
- “stanford”
- “oper”
- “administrator”
- “admin”
- “user”
- “asdfghjkl;”
- “lexis”
- “test”
- “nopassword”
- “rescomp”
- “123”
- “abc”
- “asdf”
- “football”
- “secret”
- “a”
- “1234”
- the local computer name
- the logged-on user’s SUnetID (if available)
- the logged-on user name (short form)
- the logged-on user name (long form, if available)
Registry Changes
Selecting "What Settings Will Be Changed?" from the Help Menu will automatically generate a complete changes document that will be opened in the default browser.
Example Log File
============================================================
Stanford Network Registration Tool Start Windows Version
------------------------------------------------------------
Program Version: 3.0.11.4 (Beta)
[5/29/2009 - 11:12:19 PM] Get MAC addresses...
[5/29/2009 - 11:12:21 PM] Hardware interface \DEVICE\TCPIP_{FE7DA67C-47C2-4260-9EB5-F7AEB584915E} () has been excluded: no MAC address.
Hardware interface \DEVICE\TCPIP_{9173507E-BDBD-498F-8E6D-1A55DBA1183E} (50-50-54-50-30-30) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{181EA1C3-B1B7-4054-9331-AD5168FCCD80} (33-50-6F-45-30-30) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{FB6D582A-BC84-4F7C-AB85-132EE703879C} (20-7C-20-52-41-53) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{1F4A3ABF-688D-426B-9F25-DE2281CC3658} (1E-1A-20-52-41-53) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{6AB378E2-DED2-4199-B265-B99447A8045F} (20-41-53-59-4E-FF) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{55CB2C3E-EE54-4510-B960-34354A8975A2} (02-00-54-55-4E-01) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{B3870585-50F6-4D4A-941A-9600657BF2E4} (02-00-4C-4F-4F-50) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{E3DB5241-2294-48AF-BD18-6D3FE21181EC} (00-00-00-00-00-00) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{B4A2AA34-AA20-4D9D-B37F-BF11CB74B120} (00-05-9A-3C-78-00) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{B55E8808-A3A9-4A49-91FB-B536B55A671C} (00-05-9A-3C-78-00) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{76972A4A-E8DA-42C8-995F-FAE16A2BACAD} (20-7C-20-52-41-53) has been excluded: NIC description is in blacklist.
Hardware interface \DEVICE\TCPIP_{0B69845D-2838-4A9F-8C1F-FF0F0B845F71} (1E-1A-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{72F4AF4F-7044-4220-BFAB-217CFEE86FB8} (00-13-72-9D-AA-F6) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{3189C680-D0A3-40B9-B396-22A04C8034E8} (00-13-72-9D-AA-F6) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{57CAB0CA-AE11-46F7-A2B8-3A674B51C436} (1E-1A-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{7699D643-7F55-4163-A49C-BD1155EFB13F} (1E-1A-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{CF64BCD0-3173-4872-B473-EB475BF0F0B9} (00-50-56-C0-00-01) has been excluded: MAC address is in blacklist.
Hardware interface \DEVICE\TCPIP_{5E583A8C-9B81-4C8D-9E50-76ECE6EAB395} (00-00-00-00-00-00) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{F323CB46-3278-4D32-A321-9C8AA6AD7833} (00-50-56-C0-00-08) has been excluded: MAC address is in blacklist.
Hardware interface \DEVICE\TCPIP_{24E6898B-3ABD-4521-BE13-84C6919D8C05} (00-00-00-00-00-00) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{C1BBBEA4-478F-4999-A53D-2C86383CC568} (00-00-00-00-00-00) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{F0DA2D2C-3E20-4E67-A4BF-FC6DA3992105} (00-00-00-00-00-00) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{42133D0F-6A70-11DB-BBC9-0014220F08BB} (20-7C-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{42133D11-6A70-11DB-BBC9-0014220F08BB} (1E-1A-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{1E9FF655-F700-11DC-B9A6-0013729DAAF6} (1E-1A-20-52-41-53) has been excluded: duplicate MAC address.
Hardware interface \DEVICE\TCPIP_{D74E7ABD-54F5-11DC-BCE0-EDDFD8C51C41} (00-13-72-9D-AA-F6) has been excluded: duplicate MAC address.
[5/29/2009 - 11:12:22 PM] MAC addresses: 00-13-72-9D-AA-F6=wired
[5/29/2009 - 11:12:22 PM] Active IP addresses: 171.64.18.143
[5/29/2009 - 11:12:22 PM] Primary network interface details:
MAC address: 00-13-72-9D-AA-F6
IP address: 171.64.18.143
Network mask: 255.255.254.0
Gateway address: 171.64.18.1
Gateway mask: 255.255.255.255
DHCP enabled: true
DHCP lease obtained: 5/30/2009 5:40:27 AM GMT-7
[5/29/2009 - 11:12:22 PM] Download configuration file...
[5/29/2009 - 11:12:22 PM] Home Server: snsr-test.stanford.edu
[5/29/2009 - 11:12:22 PM] Success ->File http://snsr-test.stanford.edu/hct/selfreg-config.ini downloaded OK.
[5/29/2009 - 11:12:22 PM] We have downloaded the support files today. Skip download...
[5/29/2009 - 11:12:22 PM] Requesting template variables from server.
[5/29/2009 - 11:12:22 PM] Sending the string: https://snsr-test.stanford.edu/snsr/servlet/GetPolicy?MAC=00-13-72-9D-AA-F6&00-13-72-9D-AA-F6=wired
[5/29/2009 - 11:12:24 PM] !ERROR--->The Self-Registration Server returned the following error: no reserved node found
[5/29/2009 - 11:12:24 PM] Template variables for this subnet:
[5/29/2009 - 11:12:24 PM] Final URL: <none>
[5/29/2009 - 11:12:24 PM] Post URL: <none>
[5/29/2009 - 11:12:24 PM] BigFix Required: false
[5/29/2009 - 11:12:24 PM] Sophos Anti-Virus Required: false
[5/29/2009 - 11:12:24 PM] Registered: false
[5/29/2009 - 11:12:24 PM] Check to see if the Malicious Software Removal Tool needs to be run...
[5/29/2009 - 11:12:25 PM] Most recent MSRT GUID from Microsoft KB891716: AC36AF73-B1E8-4CC1-9FF3-5A52ABB90F96
[5/29/2009 - 11:12:25 PM] Most recent MSRT GUID from local Windows registry: AC36AF73-B1E8-4CC1-9FF3-5A52ABB90F96
[5/29/2009 - 11:12:25 PM] The most recent MSRT (AC36AF73-B1E8-4CC1-9FF3-5A52ABB90F96) has already been run.
[5/29/2009 - 11:12:25 PM] No account lockout policy set. Password spoofing turned on.
[5/29/2009 - 11:12:25 PM] Reserved DNS name:
[5/29/2009 - 11:12:25 PM] Get machine name...
[5/29/2009 - 11:12:25 PM] Machine Name: TRICHOBEZOAR
[5/29/2009 - 11:12:25 PM] Get SUNet ID...
[5/29/2009 - 11:12:25 PM] SUNet ID: jstamps
[5/29/2009 - 11:12:25 PM] Get user name...
[5/29/2009 - 11:12:25 PM] User Name: jstamps
[5/29/2009 - 11:12:25 PM] Get OS version...
[5/29/2009 - 11:12:25 PM] OS Version: Windows Vista Enterprise Edition Service Pack 1
[5/29/2009 - 11:12:25 PM] Get computer make and model...
[5/29/2009 - 11:12:27 PM] Make: Dell Inc. Model: OptiPlex GX620 Type: Mini Tower
[5/29/2009 - 11:12:27 PM] STR/LDT Check Error 1. We do not appear to be running inside a virtual machine.
[5/29/2009 - 11:12:27 PM] Check virus protection status...
[5/29/2009 - 11:12:27 PM] Virus Protection: Sophos Anti-Virus 7.6.8
[5/29/2009 - 11:12:27 PM] Check OS patch level. This could take a few minutes...
[5/29/2009 - 11:12:27 PM] Current estimated network throughput is 2,796.22 Kbps.
[5/29/2009 - 11:12:28 PM] Connecting to Microsoft Windows Update server: please wait...
[5/29/2009 - 11:13:44 PM] The operating system is patched and up-to-date.
[5/29/2009 - 11:13:44 PM] Check administrator password strength...
[5/29/2009 - 11:13:44 PM] (Do)Check passwords for the following administrators: Administrator, Jay Stamps, jstamps
[5/29/2009 - 11:13:44 PM] Windows password check: bUseIpcShare=False, bXPHome=False, bXPSP2=False
[5/29/2009 - 11:13:44 PM] (Do)Windows password check: Administrator
[5/29/2009 - 11:13:46 PM] (Do)Windows password check: Jay Stamps
[5/29/2009 - 11:13:47 PM] (Do)Windows password check: jstamps
[5/29/2009 - 11:13:51 PM] 3126 passwords tried for 3 users.
[5/29/2009 - 11:13:51 PM] Check BigFix status...
[5/29/2009 - 11:13:51 PM] BigFix is installed. Version: 7.0.9.164
[5/29/2009 - 11:13:51 PM] Check Windows Vista DHCP broadcast settings...
[5/29/2009 - 11:13:51 PM] DHCP service stopped OK.
[5/29/2009 - 11:13:51 PM] (Do) Setting [SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{16FAA9E1-E6A2-4E68-96E4-49DBC4893934}] Item: DhcpConnForceBroadcastFlag
[5/29/2009 - 11:13:51 PM] (Do) Setting [SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B3870585-50F6-4D4A-941A-9600657BF2E4}] Item: DhcpConnForceBroadcastFlag
[5/29/2009 - 11:13:51 PM] (Do) Setting [SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{B4A2AA34-AA20-4D9D-B37F-BF11CB74B120}] Item: DhcpConnForceBroadcastFlag
[5/29/2009 - 11:13:51 PM] (Do) Setting [SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{CF64BCD0-3173-4872-B473-EB475BF0F0B9}] Item: DhcpConnForceBroadcastFlag
[5/29/2009 - 11:13:51 PM] (Do) Setting [SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{F323CB46-3278-4D32-A321-9C8AA6AD7833}] Item: DhcpConnForceBroadcastFlag
[5/29/2009 - 11:13:51 PM] DHCP service started OK.
[5/29/2009 - 11:14:39 PM] User has opened the bug report form.
[5/29/2009 - 11:15:03 PM] Success ->DCM settings configuration XML file downloaded.
[5/29/2009 - 11:15:03 PM] Success ->DCM configuration XML file includes 22 settings.
[5/29/2009 - 11:15:03 PM] ------------------------------------------------------------
[5/29/2009 - 11:15:03 PM] Begin changing settings...
[5/29/2009 - 11:15:03 PM] (Do)Success ->DoS attack settings: (dcmChangeEngine.CallWrapper) The setting: DoSProtect already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->DoS attack settings: (dcmChangeEngine.CallWrapper) The setting: TCPIP_KeepAliveTime already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->DoS attack settings: (dcmChangeEngine.CallWrapper) The setting: TCPIP_PerformRouterDiscovery already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->AEDebug disabled: (dcmChangeEngine.CallWrapper) The setting: AEDebug already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->IP source routing disabled: (dcmChangeEngine.CallWrapper) The setting: IPSrcRouting already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Alternate gateway detection disabled: (dcmChangeEngine.CallWrapper) The setting: DtctAndUseAltGateway already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Path MTU discovery enabled: (dcmChangeEngine.CallWrapper) The setting: EnPathMTUDiscovery already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->No name release on demand: (dcmChangeEngine.CallWrapper) The setting: NmRelOnDemand already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Protect against SYN flood attacks: (dcmChangeEngine.CallWrapper) The setting: SynAttackProtect already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->TcpMaxHalfOpen configured: (dcmChangeEngine.CallWrapper) The setting: TcpMaxHalfOpen already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->TcpMaxHalfOpenRetried configured: (dcmChangeEngine.CallWrapper) The setting: TcpMaxHalfOpenRetried already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->DLL search order optimized: (dcmChangeEngine.CallWrapper) The setting: SafeDllSearchMode already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Disable ADODB.Stream: (dcmChangeEngine.CallWrapper) The setting: DisableADODBStream already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Blank passwords allowed for console logon only: (dcmChangeEngine.CallWrapper) The setting: LimitBlankPwdLoginToConsole already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Automatic Update enabled and run daily: (dcmChangeEngine.CallWrapper) The setting: WindowsUpdate already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Automatic Update enabled and run daily: (dcmChangeEngine.CallWrapper) The setting: Windows_AU_Options already complies with the standard.
[5/29/2009 - 11:15:03 PM] (Do)Success ->Automatic Update enabled and run daily: (dcmChangeEngine.CallWrapper) The setting: Windows_AU_Schedule_Day already complies with the standard.
[5/29/2009 - 11:15:03 PM] ------------------------------------------------------------
[5/29/2009 - 11:15:03 PM] Sending to server: https://snsr-test.stanford.edu/snsr/servlet/ActivateNode?MAC=00-13-72-9D-AA-F6&00-13-72-9D-AA-F6=wired&OS=Windows+Vista+Enterprise+Edition+Service+Pack+1+&IP=171.64.18.143&MAKE=Dell+Inc.&MODEL=OptiPlex+GX620&TYPE=Mini+Tower
[5/29/2009 - 11:15:04 PM] Server Response: error=no template found for the node
[5/29/2009 - 11:15:04 PM] !ERROR--->An error occurred while attempting to contact the Self-Registration Server. (no template found for the node)
------------------------------------------------------------
User chose to cancel registration process. End Windows Version
============================================================
Computer Model Details
PC
PC model information is obtained by a WMI call that retrieves computer model information provided by the manufacturer.
Mac
Mac model information is obtained by running “sysctl hw.model” from the command line and retrieving the model from the sysctl output. Sysctl gets this string from OpenFirmware and will necessarily change as new models are released. The string that is returned is a representation of the actual Model name. For example, “PowerMac3,6” is a PowerMac G4 and "PowerMac7,2” is a PowerMac G5 See Apple documentation for an up-to-date list of translations.
Computer Type Details
PC
PC Type information is obtained by a WMI call that will retrieve one of the following:
- “Other” Could use Virtual here for VM machine.
- “Unknown”
- “Desktop”
- “Low Profile Desktop”
- “Pizza Box”
- “Mini Tower”
- “Tower”
- “Portable”
- “Laptop”
- “Notebook”
- “Hand Held”
- “Docking Station”
- “All in One”
- “Sub Notebook”
- “Space-Saving”
- “Lunch Box”
- “Main System Chassis”
- “Expansion Chassis”
- “SubChassis”
- “Bus Expansion Chassis”
- “Peripheral Chassis”
- “Storage Chassis”
- “Rack Mount Chassis”
- “Sealed-Case PC”
Mac
Mac type information is obtained by running “sysctl hw.model” from the command line and parsing the model from the sysctl output (if the model contains the string “book” it is assumed to be a laptop). The Mac type will be either “Desktop” or “Laptop”
Configuration INI File
The configuration INI file is included with the binary that is downloaded to the computer and is updated from the network at runtime. It contains information that the program will use to access support file.
Example file contents:
<su-config-file>
[Network]
IsTestServer=0
HostServer=snsr.stanford.edu
HostServerTest=snsr-test.stanford.edu
HostServerDev=snsr-dev.stanford.edu
[SupportFiles]
master_config_file=http://%HostServer%/hct/selfreg-config.ini
windows_av_file=http://%HostServer%/hct/anti_virus.ini
mac_av_file=http://%HostServer%/hct/mac_anti_virus.ini
password_check=http://%HostServer%/hct/pchk.bin
windows_dcm_xml=http://%HostServer%/hct/suhc_settings.xml
mac_dcm_xml=http://%HostServer%/hct/mac_suhc_settings.xml
macaddr_addwhite_list=http://%HostServer%/hct/suhc_whitelist.txt
macaddr_addblack_list=http://%HostServer%/hct/suhc_blacklist.txt
patch_exclude_list=http://%HostServer%/hct/patch_exclusions.txt
self-reg-server=https://%HostServer%/snsr/servlet/ActivateNode
self-reg-server-chk=https://%HostServer%/cgi-bin/hc_post
template_var_request=https://%HostServer%/snsr/servlet/GetPolicy
windows_update_help=http://update.microsoft.com/microsoftupdate
HelpText=Please contact your Local Network Administrator (LNA) for assistance with registering your computer. If you don't know who your LNA is or if you need other assistance please call (650) 725-HELP (4357).
sav_pc_url=http://www.stanford.edu/services/selfreg/hct_redirects/antivirus.html
sav_pc_vista_url=http://www.stanford.edu/services/selfreg/hct_redirects/antivirus.html
sav_mac_url=http://www.stanford.edu/services/selfreg/hct_redirects/antivirus.html
bigfix_pc_url=http://www.stanford.edu/services/selfreg/hct_redirects/bigfix.html
bigfix_mac_url=http://www.stanford.edu/services/selfreg/hct_redirects/bigfix.html
kerberos_pc_url=http://www.stanford.edu/services/ess/pc/kfw.html
kerberos_mac_url=http://www.stanford.edu/services/ess/mac/kfm.html
; information about the Malicious Software Removal Tool, including the current GUID, is at http://support.microsoft.com/kb/891716/
msrt_pc_file=http://%HostServer%/hct/Windows-MSRT.exe
msrt_pc_x64_file=http://%HostServer%/hct/Windows-x64-MSRT.exe
msrt_pc_file_size=9615808
msrt_pc_x64_file_size=10038720
msrt_pc_most_recent_guid=AC36AF73-B1E8-4CC1-9FF3-5A52ABB90F96
[Options]
check_private_net=true
use_wsus_server=false
</su-config-file>


