Use Case Scenarios
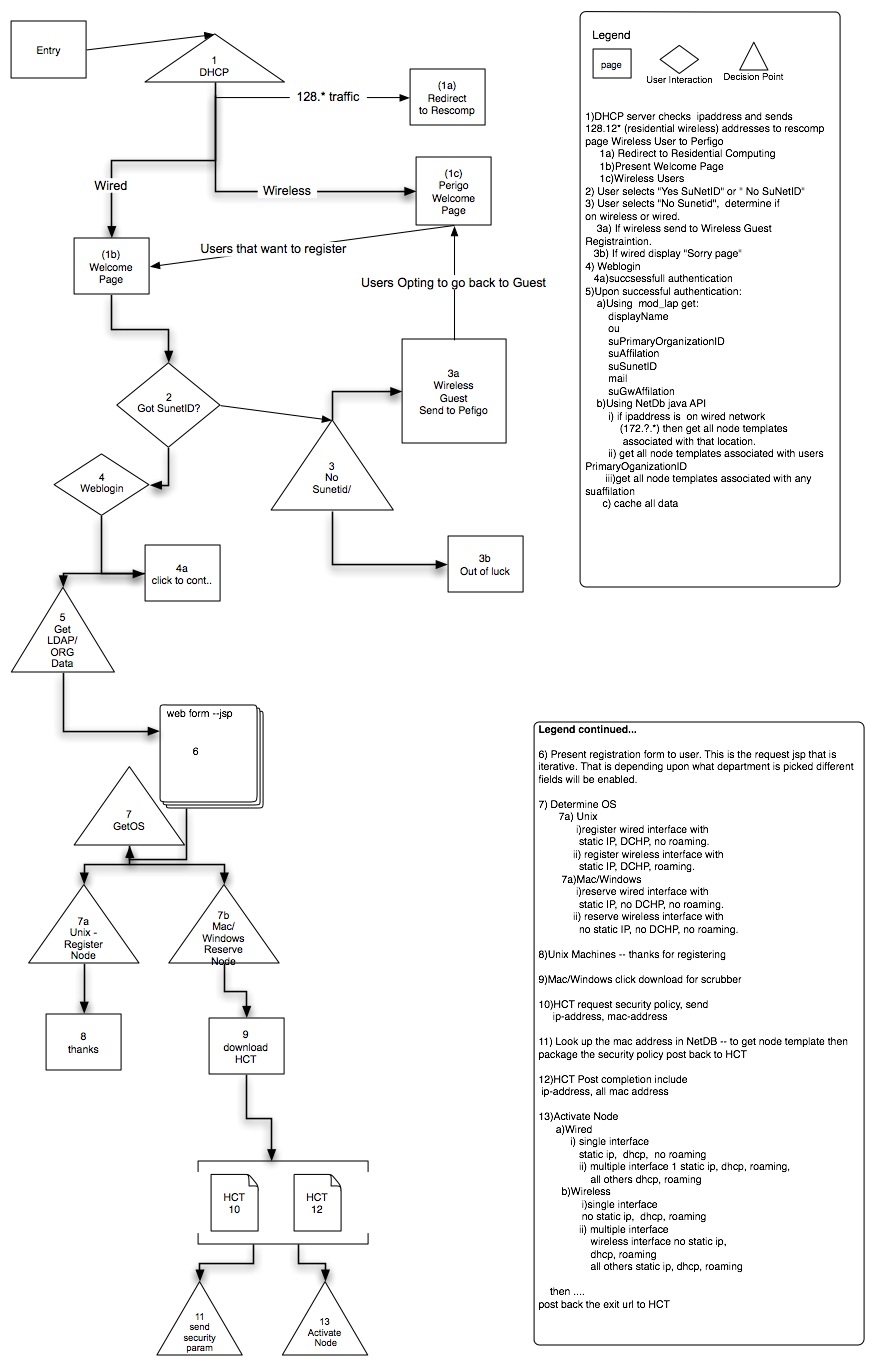
Scenarios
Scenario 1:
User opens a browser on a Unix machine with single interface from a wired network User will go through steps 1) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7a) i) -> 8) in the flow chart above
Scenario 2:
User opens a browser on a Unix machine with single interface from a wireless network User will go through steps 1) -> 1c) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7a) ii) -> 8) in the flow chart above
Scenario 3:
User opens a browser on a PC/Mac machine with single interface from a wired network User will go through steps 1) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7b) i) -> 9) -> 10) -> 11) -> 12) -> 13) a) i) in the flow chart above
Scenario 4:
User opens a browser on a PC/Mac machine with single interface from a wireless network User will go through steps 1) -> 1c) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7b) i) -> 9) -> 10) -> 11) -> 12) -> 13) b) i) in the flow chart above
Scenario 5:
User opens a browser on a PC/Mac machine with multiple interfaces from a wired network User will go through steps 1) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7b) i) -> 9) -> 10) -> 11) -> 12) -> 13) a) ii) in the flow chart above
Scenario 6:
User opens a browser on a PC/Mac machine with multiple interfaces from a wireless network User will go through steps 1) -> 1c) -> 1b) -> 2) -> 4) -> 5a) -> 5b) -> 5c) -> 6) -> 7b) i) -> 9) -> 10) -> 11) -> 12) -> 13) b) ii) in the flow chart above
Scenario 7:
User with no Sunetid opens a browser on any machine from wired network User will go through steps 1) -> 1b) -> 2) -> 3) -> 3b)
Scenario 8:
User with no Sunetid, who is not a wireless guest opens a browser on any machine from wireless network User will go through steps 1) -> 1c) -> 2) -> 3) -> 3b)
Scenario 9:
User with no Sunetid, who is a wireless guest got redirected to hostreg site, but opts to go back to perfigo User will go through steps 1) -> 1c) -> 2) -> 3) -> 3a)
Scenario 10:
User comes from Rescom network User will go through steps 1) -> 1a)
Scenario 11:
User directed to the site by Rescom host reg to download Health Check Tool.


