Security 2 - Phishing
2. - Phishing Attacks
- "Phishing" is a type of attack where the bad guy tricks you into typing your password into a bad guy site, thus the bad guy gets your password
- Phishing and dictionary attacks (previous section) are two major ways that people's accounts are broken into
- You have probably received many phishing emails. The phishing email most often includes a link to a page such as the one shown below
Here is an example phish site from one of the many paypal phishing emails in my inbox:
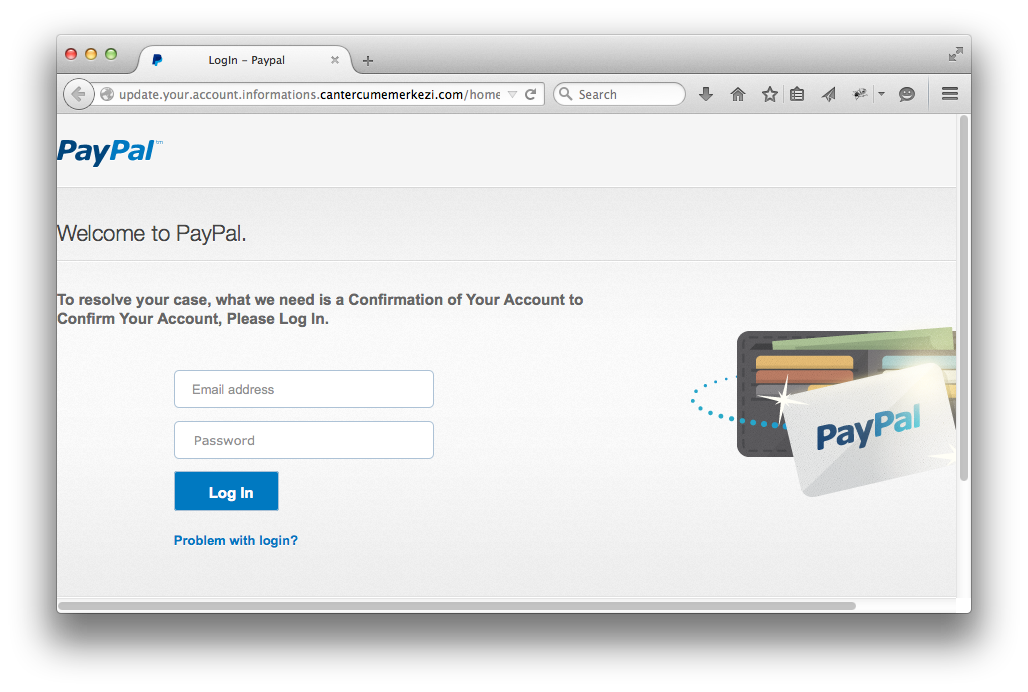
- The above is phishing site, not the real paypal site. If you type your username and password into the phishing site, they are sent to the bad guy who can use them to break into your account.
- The graphics and coloring are correct. Those are trivial for the bad guys to copy and mean nothing.
- The title of the tab - "Paypal Login" - is also meaningless.
- How do you detect that this is a phishing site? Look at the url, near the top of the browser window. Does it say "www.paypal.com"? Checking that is your one defense.
- The word "phishing" is a little joke. The bad guy is "fishing" for you.
- Bad guys are skilled at writing provocative emails, prompting you to click, e.g. "fraud alert, click immediately"
- Alternately, the bad guy might sprinkle links to the phishing site across web in forum comments and anywhere else they can. Anything to get people to visit the page and get phished.
Probably the most common form of attack. The email is forged to appear from someone you might trust -- including logos etc -- I have gotten ones which I personally found quite convincing. I had to slow down and really pay attention to realize that it was a phishing attempt. It does not help that ATT, Schwab, Citigroup, etc. do in fact send you email all the time about your accounts.
Fake ATM Machine -- Real World Analogy
- Funny "phishing" crime in real life
- Fake ATM in front of bank .. prints error message, but records card details and PIN for bad guy
Criminals put up a fake ATM machine made of plywood in front of a real ATM, with a "under construction" sign. The victim would put their card into the fake ATM and type in their PIN. Then the machine would print an "out of order" message and give the card back. The bad guys in this way collected all the card numbers and PINs and drained the accounts over the weekend. This is a nice real-world analog of fake-site phishing.
Avoiding Phishing
- Don't trust urls in emails or sites when they lead to a login page
- The bad guy is hoping that when the username/password fields appear in front of you, you will just type it in out of a habit. When asked for your password, slow down for a moment and look.
- Technique 1: Scrutinize the url near the top of the browser window
- The bad guy url will try to look legitimate but it is not the correct url, e.g. www.ebay.bad-guy.ru is not the official ebay site, which should end in "ebay.com"
Avoiding Phishing - URL / typing
- The screenshot above shows this bad guy technique. The bad guy added a series of plausible words to the left of the domain name, hoping you would stop reading: "update.your.account.information.cantercumemerkezi.com". Does "cantercumemerkezi.com" seem like a site where you should be typing your paypal password?
- The 2 rightmost words of the url define the organization controlling the url, so that's what you are checking.
- Safe: accounts.google.com, login.gmail.com
- Not safe: accounts.google.bad-guy.ru, gmail.login.quicksite.hk
- Technique 2: (more secure) Type the url into your browser yourself -- if the email claims you need to log into ebay, go to your browser manually and type in "www.ebay.com". This is what I tell my parents to do, as it's a simple rule. In this way you sidestep the www.ebay.bad-guy.ru url the bad guy placed in the email.
- Chrome and the other major browsers have an ongoing effort to detect and warn users about phishing sites in realtime. Sometimes this will save you with a warning about a phishing page. If you see a phishing site, you can use the "report web forgery" menu item in our browser to report the site, contributing against the bad guys.
- Look for https in the url (below)
Email Phishing vs. 2016 Election
- I believe the theory that Russia wants to discredit the idea of democracy
- Breaking into someone's email account was a good strategy
-Lots of emails to dig through with any one success, try it everyone
- John Podesta got a fake google-account email reset
- His IT person meant to write "illegitimate" but wrote "legitimate" - typo of the century!
- Apparently Podesta used same password to secure twitter, so they got that too
- Podesta did not have two-factor enabled
- New York Times
- email here
- typo here
HTTPS
- HTTPS - "secure" variant of HTTP to transfer the bytes of a web page over the internet
- HTTPS does two things:
- a. HTTPS requires some paperwork to set up, so that the domain www.schwab.com domain name really is coming from the Schwab organization.
-Helps prevent phishing, but the user still needs to look at the url
-e.g. Checking that it's www.schwab.com not www.schwarb.bad-guy.ru
- b. HTTPS encrypts all the traffic, so interception of the bytes does not yield anything intelligible
HTTPS is the "secure" http variant, https://www.ebay.com/. In particular, the server must hold a certificate which is verified beforehand by an authority that the server really represents www.ebay.com or whatever. You have to pay money and file some paperwork to get an https certificate -- hard for a bad guy to do, although not impossible. The idea with https is that the user can see the identity of who they are talking to. In the browser interface, https is typically accompanied by a little lock icon, and some banks etc. mention to their users to look for the lock. Having users pay attention 100% of the time is not a perfect security solution, but it helps.
Encryption vs. Bad Guy Packet Eavesdropping
- "Encryption" is a way of scrambling data before it is sent out in packets, so that even if intercepted, they are meaningless
- HTTPS provides encryption, in addition to its url-verification feature
- Example: this is a picture where I went to Starbucks and logged in to their free Wi-Fi. Then I went to the www.schwab.com home page and type typed in my password to log in
- My password was sent out in Wi-Fi radio packets sent from my laptop to the Wi-Fi router and on to www.schwab.com. These packets could be intercepted by all the other laptops at starbucks at that moment.
- Probably several laptops there were infected with malware, and malware often specifically targets financial info (e.g. Schwab)
- Could someone there have gotten my password out of a packet?
- No -- HTTPS encrypted all the packets before they were sent from my laptop
- Note if my machine had malware on it, it could steal my password as a typed it in. HTTPS only takes care of the networking.
When you go on to wifi and visit a web page and type something in ... the packets for all that are just being broadcast in the room, so anyone nearby can observe the packets, listening in (recall the ethernet-packet-broadcast material from the networking section). For the most part, this is harmless. In some cases, say when you are typing in a credit card number, you want the communication to be encrypted (encoded), so that someone listening in cannot read it. The https scheme above also does encryption, so you will notice that when you go the page to type in a credit card number, the url begins with "https://". On such page, all the packets are encrypted, so someone can listen and see the packets, but they will appear to be random garbage. The eavesdropper cannot unscramble the packets to see what's inside, or forge a packet. So Https blends two security provisions -- (a) verifying that it really is the www.mybank.com or whatever server on the other end and (b) encrypting all the packets of the communication.

